Security
Our customers use SockPuppet for sensitive, mission-critical investigations that demand absolute confidentiality. Whether you’re tracking threat actors, collecting digital evidence, or conducting undercover engagements, you need a platform that enables those operations without ever exposing your organization.
SockPuppet was built to empower investigations while ensuring complete privacy, data isolation, and technical integrity. Your data is yours alone. We are never a party to it.
Your Data, Your Keys
Every Alias environment — including Virtual Desktops and Virtual Phones can be encrypted using FIPS 140-2–validated algorithms with AES-256-bit encryption at rest and TLS 1.3 in transit.
Customers can take that further by using their own encryption keys, stored and managed within their internal Key Management System (KMS), ensuring:
This architecture ensures that your investigative activity, evidence, and communications remain private — controlled by you, and protected by FIPS-grade encryption end to end.

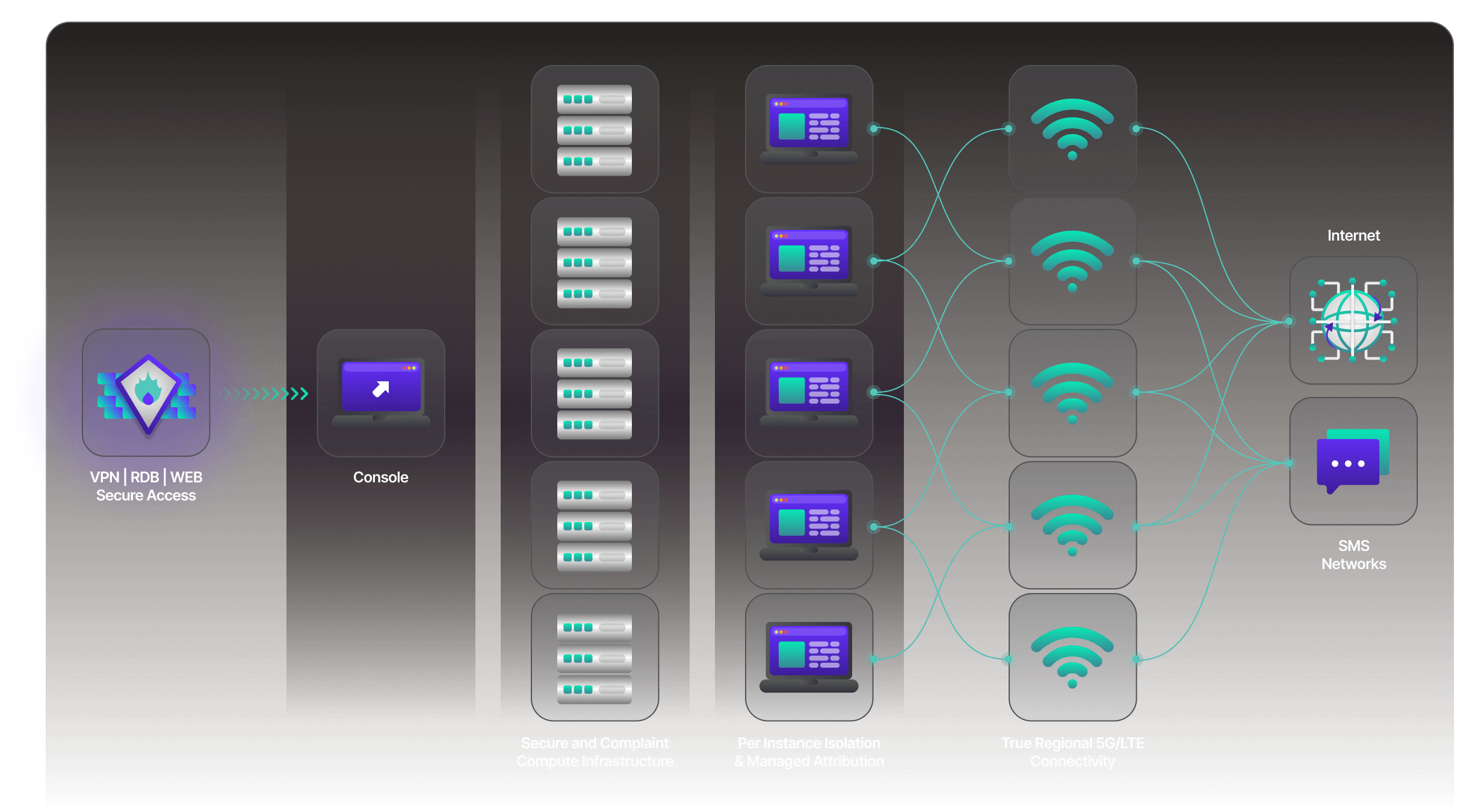

Independent Encryption Across Every Component
You can manage your own encryption keys for every subsystem in Alias, ensuring full separation of data domains:
Each subsystem operates under independent encryption scopes, providing layered defense and compartmentalization. Even in the event of a single key or credential exposure, other data remains cryptographically isolated.
Private Infrastructure & Custom Deployments
For customers requiring maximum control, SockPuppet offers custom deployment options, including:
We also support hybrid and on-premise models for agencies and enterprises that must meet internal or legal data-residency mandates — without losing access to our managed attribution and operational features.
Certified Security & Compliance
SockPuppet’s infrastructure and processes are independently audited and verified against recognized industry and government frameworks.


These certifications and standards confirm that every byte of data you handle through SockPuppet is protected to the highest technical and procedural levels.
Get Started with SockPuppet Today
Let’s build your next identity together.
Contact SockPuppet today to discuss your operational needs and see how Alias can power your next investigation.